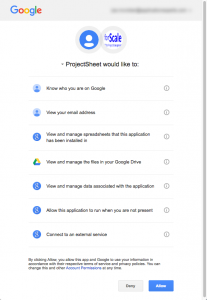
Yesterday I blogged about my concerns with a free Google Apps extension that required the very scary googleapis.com/auth/drive permission. When you give a Google Apps extension this permission, it can read, write, or delete any documents you have access to in Google Drive.
I inquired why the extension needed so much authorization, and the developer replied quickly. He agreed! The permission was only required for a specific feature that didn’t seem super important for the free version. So he removed the feature and permission requirement. In less than 24 hours!
Three take-aways for me:
- Use your brain when giving an app or website permission to access your information in the cloud. Why do they need the authorization they are requesting? This is particularly true when using Facebook or Google+ to login to other sites.
- Push back, you never know when you’ll find somebody reasonable on the other end. Or maybe you will learn more about why the authorization is necessary.
- Definitely try ProjectSheet Planning from forScale and support reasonable developers who understand cloud security concerns.
Now I’m happy and can white list the extension for my company to use.