
Today Charlie and I shut down the CodexVT website. It sure was fun teaching coding and video game development to middle schoolers all those years ago.
Teaching 8th Grade computer programming under Shelter in Place is working just fine. My class is creating a “Ready Player One” style quest with 3 video games linked together. They are really motivated because this end-of-the-year project will become one of the celebration activities at the end of school. That’s right: no Field Day, no Graduation practice, so you need something fun and virtual to do with students during school hours after exams.
With my students coding their hearts out on Construct.net, I had time to work on improving the user experience for ABC Essentials – our wellness app. Building it without code was interesting. Now that I’m using the whole toolset, it is SO MUCH BETTER. The team at Salesforce.com really nailed the developer experience with Lightning Web Components (LWC) and VS Code as the development environment. The platform had always been great for users, now it is first class for developers too!
Check out the new version and download the updated package with Apex code, Triggers, Batch Jobs, and Lightning Web Components.
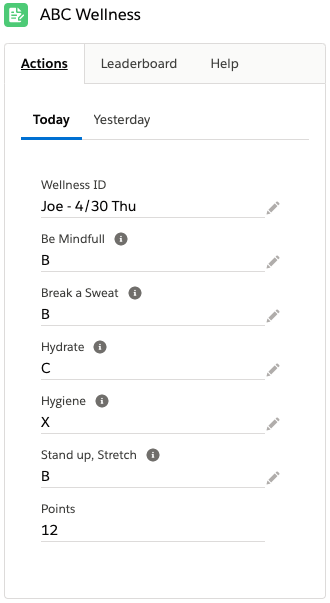
Spring break this week for my high school teaching so I decided to create a free little wellness app on Salesforce.com. If you are an organization that uses Salesforce and you want to launch weekly work-from-home wellness contents, then “ABC Essentials” could be just the ticket.
My project team included my sister and her daughter. They are smart and healthy lifestyle people, so they came up with 10 actions we can all consider each day to improve our social, emotional, and physical wellness. We shrunk it down to 5 in the product, but a skilled Admin could easily change or add other actions into the data model.
You can find out more here and download the unmanaged package into a dev org or sandbox to play with it. Note that this first version is just clicks, no code, plus a little Process Builder. It was interesting to see how far we could go with Lightning and Mobile while also being 100% backward compatible with Classic.
Next step is to do a Lightning-required version and take advantage of Screen Flows, Global Actions, and Lightning Components. Should be a fun upgrade! Stay tuned…
This year at Dreamforce, the theme was “together” and the most impressive technical innovation was how polished you could make digital marketing campaigns and community sites. In the past, it seemed like Salesforce marketing tools were more efficient than beautiful. Now they are both.
Check out the keynote starting at around 1h:10m with Brett Taylor. He will demo how Louis Vuitton is using Commerce Cloud and Einstein to build personalized phone apps with digital assets stored in their central content management system. I’ve played around with some of this in the labs and it is really cool.
Scary times with Facebook and Cambridge Analytica in the crosshairs for leveraging “private” information about users. Other people are freaking out at the amount of data Google has been collecting every time you use an Android phone. I’m sure Apple is doing the same.
One more negative and then I’ll turn this positive. Have you seen what AR (Augmented Reality) is doing for our ability to do real-time video editing? Check out futureoffakenews.com. This is morphing technology where two things are happening simultaneously. First, an actor is delivering a speech and his mouth is being superimposed on the mouth of somebody famous. Second, the actor’s words are being transcoded into the voice and inflection of the famous person. The complete effect is a little off, but I’m sure the technology will get better every year. At some point in the not too distant future, we will be able to create fake broadcasts of speeches being delivered in realtime. One news network will be able to change — in realtime — what their favorite (or least favorite) politician is saying. What and who do you believe at that point?
Take this down a level to the average citizen. How do we defend ourselves against:
One solution might be taking personal control over your already lost privacy. How about we start encoding all our location data on a blockchain (so it can’t be altered). If personal location and activity data was captured by each person’s phone and blockchain encoded, then I’d be able to prove I wasn’t at that hotel bar where I supposedly propositioned my female colleague.
How about all surveillance video be blockchain encoded so it can’t be altered. Build blockchain algorithms into the ASIC that does the compression. We need some way to ensure that our digital records are real and a blockchain might be just the ticket.
The way we defend the truth might be to memorialize the truth in ways that can be verified as genuine. That means we need to be OK with the truth, the whole truth, and nothing but the truth being discoverable by both our friends and our foes. How does that sit with you?
There are no excuses left. Every website should be using SSL. I spent a few hours this weekend and got McVicker Group, McVickerNet, and CodexVT all using a SSL for Free cert.
Not that I do anything super high security on these sites, but it makes me feel better to have an extra layer of identification on my web properties.
Once you have the cert installed, the easiest way to force all your traffic to SSL is by adding the following .htaccess code.
RewriteEngine On
RewriteCond %{HTTPS} off
RewriteRule ^(.*)$ https://yourdomain.com/$1 [R=301,L]
Remember to backup your .htaccess file before making changes and swap out “yourdomain.com” in the last line.
If you are running WordPress, you will probably need to update internal links too. I used a great plugin, SSL Insecure Content Fixer, and let it is fix all content and scripts.
 Verizon Enterprise does an annual data breach analysis and it is pretty much a gold standard for information and trends in cybercrime. This year’s report is chock full of easy-to-digest charts and good information.
Verizon Enterprise does an annual data breach analysis and it is pretty much a gold standard for information and trends in cybercrime. This year’s report is chock full of easy-to-digest charts and good information.
I recommend everyone who cares about privacy and data security download and read at least the executive summary.
Most interesting statistics to me were:
Combining those two findings really makes the case that every company should require 2 factor authentication.
Well, I got too busy to blog when I returned from Google Next. Here are some of my favorite sessions.
TensorFlow and Deep Learning without a PhD was definitely worth the price of admission. Here are the two videos.
Firebase was also super impressive. My son and I have already built the tutorial chat application and are turning it into a universal translator based on geolocation of clients.
You can subscribe to the Google Next 2017 Channel on YouTube and see all sorts of highlights.
Enjoy!
I’ve spent the last week in San Francisco at Google Next 2017. It is nice to be at Moscone for something smaller than DreamForce. 10,000 people this week feels so much more manageable than 140,000 at my last Salesforce.com conference.
Big things coming for G Suite (fka Google Apps). My favorite new announcement is App Maker. It is totally Microsoft Access for the web. You can build web apps using drag and drop and add App-Script where you need something really special to happen. Only bummer is they are planning on limiting it to G Suite for Business (the $10/user plan).
I’ll do a series of blog posts over the next week with links to my favorite sessions. Machine Learning is definitely something Google is trying to win. They rolled out a set of APIs with fully trained models for Speech, Translation, Image Recognition, and even Video Classification.
I’m a big advocate of cloud data security. Cloud service providers are, in general, better at security than their customers. So your data is safer in the cloud than it is on your local machine or network.
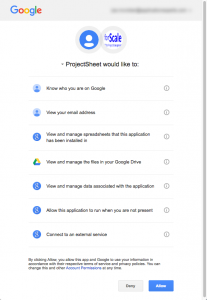
However, it doesn’t feel that way, does it? Yesterday a colleague showed me a cool plug-in for Google Sheets that creates simple GANTT charts using spreadsheet data. When I installed the plug-in, it prompted me for the permissions it needed to function. Take a look at the list on the right (click to enlarge).
Numbers 1 to 3 are not a big deal to me. I’m happy to have this plug-in work on the files where I use it. Number 4 is scary: this plug-in can look at ALL my google drive files. Number 6 and 7 make it even scarier: this thing can run whenever it wants and connect to an external service.
This plug-in appears fine today. But tomorrow, an evil developer could change their software without telling anyone. The software could start to scan any of my Google Drive documents and send that data to an external service.
I’m going to do more research on these permissions and see if my concerns are real or just cloud paranoia. Stay tuned.